By: Derek Colley | Updated: 2013-05-30 | Comments (17) | Related: 1 | > Encryption
Problem
You work in a shop that puts business or application logic in the SQL Server using stored procedures, views and functions to return values to the calling applications or perform tasks. This is not unusual in companies that use the SQL Server layer to perform business tasks, such as finance operations, or incorporate application functionality into the programmability layer. You wish to preserve secrecy on some procedures, views or functions in order to maintain security.
Solution
SQL Server stored procedures, views and functions are able to use the WITH ENCRYPTION option to disguise the contents of a particular procedure or function from discovery. The contents are not able to be scripted using conventional means in SQL Server Management Studio; nor do the definitions appear in the definition column of sys.sql_modules. This allows the cautious DBA to keep stored procedures and functions securely in source control and protecting the intellectual property contained therein. This tip will focus on encrypting and decrypting a user-defined function.
Encrypting a UDF
To encrypt a user-defined function, simply add WITH ENCRYPTION to the CREATE FUNCTION statement (after the RETURNS element). Throughout this tip, I will be building an encrypted UDF (and decrypting it) to demonstrate the principle.
First, create the UDF. Here's mine - it's a simple module that accepts an input string and returns the encrypted varbinary hash value. There are two vital pieces of information here that MUST NOT be given away to the user of the function - the encryption standard, and the salt.
CREATE FUNCTION dbo.getHash ( @inputString VARCHAR(20) )
RETURNS VARBINARY(8000)
AS BEGIN
DECLARE @salt VARCHAR(32)
DECLARE @outputHash VARBINARY(8000)
SET @salt = '9CE08BE9AB824EEF8ABDF4EBCC8ADB19'
SET @outputHash = HASHBYTES('SHA2_256', (@inputString + @salt))
RETURN @outputHash
END
GO
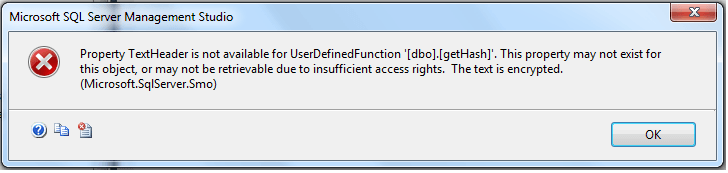
In this example the salt is fixed and an attacker, given the encryption standard (SHA-256) and the salt, could be able to decrypt the hash into plaintext. We can view the definition of a function by finding it in SQL Server Management Studio, right-clicking and scripting out the function:

The attacker can also use sp_helptext, or query sys.sql_modules if he/she knows the function name:
SELECT definition
FROM sys.sql_modules
WHERE definition LIKE ('%getHash%')
There is some protection built in; by using role-based security or sensibly allowing the least required privileges to users, the attack surface can be lessened as the VIEW DEFINITION permission is required (or ownership of the function) in SQL Server 2005 upwards. Note in earlier versions, this permission is not required. The user may also have the permission granted implicitly by holding other permissions on the object. (See 'Metadata Visibility Configuration' at http://msdn.microsoft.com/en-GB/library/ms187113.aspx for more detail).
We can amend the function definition like so:
ALTER FUNCTION dbo.getHash ( @inputString VARCHAR(20) ) RETURNS VARBINARY(8000) WITH ENCRYPTION -- rest of function here
Note that WITH ENCRYPTION occurs after RETURNS, not before. With stored procedures, the WITH ENCRYPTION option occurs immediately after the CREATE PROCEDURE x ( @somevar) statement.
With our encrypted function we can attempt to script it out in SQL Server Management Studio again, or look at sys.sql_modules. Here's what we get:
Querying sys.sql_modules definition column for this function returns NULL. Executing sp_helptext returns the error:
The text for object 'dbo.getHash' is encrypted.
Note the UDF is exactly as effective as it was before - we can still call it and return a value:
I'm using an undocumented stored procedure here called fn_varbintohex to convert the VARBINARY output from my function into a hexadecimal format, for portability between applications and clarity - it's not directly relevant to this example. Normally the VARBINARY output of HASHBYTES is passed directly to the calling application.
Decrypting a Function
Firstly, open a Dedicated Administrator Connection (DAC) to SQL Server. Using SQL Server Management Studio, this is easily done by prefixing admin: to the connection string upon connection of a query window. Note that the DAC can only be used if you are logged onto the server and using a client on that server, and if you hold the sysadmin role. You can also get to it by using SQLCMD with the -A option. Note: DAC won't work unless you're using TCP/IP; you'll get this rather cryptic error (in both SQLCMD and SSMS):
Sqlcmd: Error: Microsoft SQL Server Native Client 11.0 : Client unable to establish connection because an error was encountered during handshakes before login. Common causes include client attempting to connect to an unsupported version of SQL Server, server too busy to accept new connections or a resource limitation (memory or maximum allowed connections) on the server.
If you can't access the server directly for whatever reason, you can enable remote administrative connections (a remote DAC) as follows. You'll still need to use TCP/IP:
exec sp_configure 'show advanced options', 1 RECONFIGURE WITH OVERRIDE exec sp_configure 'remote admin connections', 1 RECONFIGURE WITH OVERRIDE
The procedure for decryption comes in three steps. First, get the encrypted value of the procedure definition from sys.sysobjvalues (via the DAC connection). Secondly, get the encrypted value of a 'blank' procedure, where the definition is filled in by '-'. Thirdly, get the plaintext blank procedure statement(unencrypted). Now XOR them together (XOR is the simplest of decryption procedures and forms the basis of many algorithms including MD5) as shown below to retrieve the output of the procedure. You'll find my take on this algorithm in the code example below:
-- Connect using the DAC then execute the below
SET NOCOUNT ON
GO
ALTER PROCEDURE dbo.TestDecryption WITH ENCRYPTION AS
BEGIN
PRINT 'This text is going to be decrypted'
END
GO
DECLARE @encrypted NVARCHAR(MAX)
SET @encrypted = (
SELECT imageval
FROM sys.sysobjvalues
WHERE OBJECT_NAME(objid) = 'TestDecryption' )
DECLARE @encryptedLength INT
SET @encryptedLength = DATALENGTH(@encrypted) / 2
DECLARE @procedureHeader NVARCHAR(MAX)
SET @procedureHeader = N'ALTER PROCEDURE dbo.TestDecryption WITH ENCRYPTION AS '
SET @procedureHeader = @procedureHeader + REPLICATE(N'-',(@encryptedLength - LEN(@procedureHeader)))
EXEC sp_executesql @procedureHeader
DECLARE @blankEncrypted NVARCHAR(MAX)
SET @blankEncrypted = (
SELECT imageval
FROM sys.sysobjvalues
WHERE OBJECT_NAME(objid) = 'TestDecryption' )
SET @procedureHeader = N'CREATE PROCEDURE dbo.TestDecryption WITH ENCRYPTION AS '
SET @procedureHeader = @procedureHeader + REPLICATE(N'-',(@encryptedLength - LEN(@procedureHeader)))
DECLARE @cnt SMALLINT
DECLARE @decryptedChar NCHAR(1)
DECLARE @decryptedMessage NVARCHAR(MAX)
SET @decryptedMessage = ''
SET @cnt = 1
WHILE @cnt <> @encryptedLength
BEGIN
SET @decryptedChar =
NCHAR(
UNICODE(SUBSTRING(
@encrypted, @cnt, 1)) ^
UNICODE(SUBSTRING(
@procedureHeader, @cnt, 1)) ^
UNICODE(SUBSTRING(
@blankEncrypted, @cnt, 1))
)
SET @decryptedMessage = @decryptedMessage + @decryptedChar
SET @cnt = @cnt + 1
END
SELECT @decryptedMessage
If you still cannot access via DAC or prefer a code-based approach, then you can use one of a number of freeware third-party .NET-based decryption software packages to do this for you. The blog Sqljunkieshare also purports to have a method of doing this (code untested) that looks viable - you can find the link here:
http://sqljunkieshare.com/2012/03/07/decrypting-encrypted-stored-procedures-views-functions-in-sql-server-20052008-r2/ (use at your own risk)Next Steps
- SQLMAG: Decrypting a Stored Procedure: http://sqlmag.com/sql-server/decrypt-sql-server-objects
- CREATE PROCEDURE from Books Online: http://msdn.microsoft.com/en-us/library/ms187926.aspx
- CREATE FUNCTION from Books Online: http://msdn.microsoft.com/en-us/library/ms186755.aspx
- SQL Server Stored Procedure Tutorial and Example: http://www.mssqltips.com/sqlservertutorial/160/sql-server-stored-procedure/
- Getting Started with SQL Server Stored Procedures:
http://www.mssqltips.com/sqlservertip/1495/getting-started-with-sql-server-stored-procedures/
About the author
 Dr. Derek Colley is a UK-based DBA and BI Developer with more than a decade of experience working with SQL Server, Oracle and MySQL.
Dr. Derek Colley is a UK-based DBA and BI Developer with more than a decade of experience working with SQL Server, Oracle and MySQL.This author pledges the content of this article is based on professional experience and not AI generated.
View all my tips
Article Last Updated: 2013-05-30