By: Daniel Farina | Updated: 2018-03-21 | Comments | Related: > Security
Problem
You probably have heard recently about two different vulnerabilities on processors called Meltdown and Spectre that allows hackers to access the memory space of every process on any operating system. Being aware of that, you may be asking yourself a lot of questions. Just to mention a few: What are those vulnerabilities? Are my SQL Server instances affected? How can I solve this? Is there a patch? What are the effects of these vulnerabilities and their respective patches on SQL Server performance? Should I patch my systems?
This tip is aimed to give you the tools so you can answer those questions and decide what is best for your environment.
Solution
Recently we were aware of two major vulnerabilities discovered by Google’s Project Zero Team that were named Meltdown and Spectre. At first the notice created some fear, which was increased when media published that Intel's CEO, Brian Krzanich, sold a significant position of his Intel shares prior to making public the issue of these vulnerabilities (Intel CEO’s Stock Sales May Warrant SEC Examination, Bernstein Says Optics on Intel CEO Stock Sale Are `Indefensible' ).
Due to those facts, the situation looked worse than it was, but as time passed and patches came to light our uncertainty settled a little and allowed us to think and recap on this matter.
In order to know the impact of these vulnerabilities on SQL Server, first we must understand what these vulnerabilities are and how do they work and to do so we need to know what about a Side Channel Attack.
What is a Side Channel Attack?
By definition, a Side Channel Attack is any attack based on information gained from the physical implementation of a computer system, rather than weaknesses in the implemented algorithm itself. In other words, these types of vulnerabilities are hardware dependent. That makes the fix process more arduous and complicated, because the underlying problem is not (in this case) in the SQL Server code per se.
Meltdown and Spectre
Meltdown and Spectre are a class of Side Channel Attacks that rely on what is known as Speculative Execution and Out of Order Execution. This is a kind of optimization on which the CPU performs a task without knowing if that task will be needed. Modern CPUs in order to save execution time on conditional branches, execute both branches in advance meanwhile waiting for the result of the condition that will signal which of the branches is the right one to follow and which must be discarded.
I created the following image to show you how Out of Order Execution works. There is a control thread that has two branches. Each branch is executed by an Execution Unit. This happens internally in the processor, in other words this is something that happens without the programmer being aware. Then the thread decides which branch is the right one to follow.
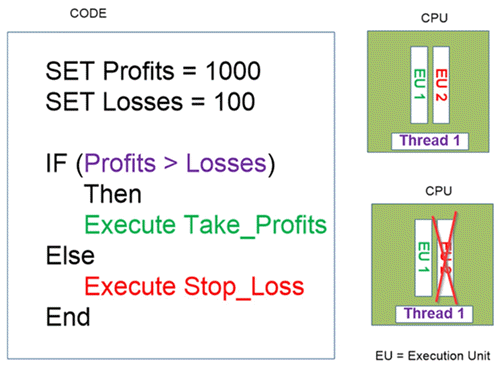
Although these vulnerabilities may look the same, there are differences amongst them. The most important difference is the level at which the vulnerabilities compromise the system.
Meltdown
This is the most compromising vulnerability because it exploits a bug in the design of Intel microprocessors. It allows a potential attacker to read the whole physical memory from a user process. Processors have levels of privilege often called Protection Rings that serve to separate the level of access to the system resources. Operating systems like Windows and Linux use these protection rings to separate the kernel space and the user space.
The fact that Meltdown allows a user process to access protected memory implies that it may be possible on a Virtualized environment to access the hypervisor from one of the virtual machines. In other words, an attacker will be able to access all the virtual machines from the hypervisor.
In order to protect your system from Meltdown you will need to apply a firmware or microcode update, remember that this is hardware related vulnerability. If you have a Linux system you can apply a microcode update by downloading the files from Intel https://downloadcenter.intel.com/download/27337/Linux-Processor-Microcode-Data-File?product=873 or by running the following:
sudo apt install intel-microcode
If your system is Windows you should apply Microsoft patches. This will update your CPU microcode to the right level according to your processor.
Spectre
The Spectre vulnerability does not allow the user mode processes to read kernel memory like what happens with Meltdown. But Spectre allows the code running on a user process to access data when it shouldn't. In layman’s terms, on a user process a thread can access the data of all its other threads. The easiest example is a web browser: You can have a few tabs opened, when each tab has its own thread, and a new tab that loads a bogus web page is able to access the data of the other tabs.
Spectre is not hardware related, so each application provider must provide their own patch for the application. Microsoft released Spectre patches for SQL Server. Also Microsoft released an update for Visual Studio and its compiler (https://blogs.msdn.microsoft.com/vcblog/2018/01/15/spectre-mitigations-in-msvc/) so software providers can recompile their applications and redistribute the patched binaries.
SQL Server Patches
Microsoft has launched patches for SQL Server for versions 2008 and above.
| SQL Server Version | Link to Patch |
|---|---|
| SQL Server 2017 | Cumulative Update 4 for SQL Server 2017 |
| SQL Server 2016 | Cumulative Update 7 for SQL Server 2016 SP1 |
| SQL Server 2014 | Cumulative Update 10 for SQL Server 2014 SP2 |
| SQL Server 2012 | Description of the security update for SQL Server 2012 SP4 GDR: January 12, 2018 |
| SQL Server 2008 R2 | Description of the security update for SQL Server 2008 R2 SP3 GDR: January 6, 2018 |
| SQL Server 2008 | Description of the security update for SQL Server 2008 SP4 GDR: January 6, 2018 |
Performance Issues
Let’s think about this. If these vulnerabilities exploit optimization methods known as Speculative Execution and Out of Order Execution, what can we infer about this? The answer is easy: We must disable those optimizations. In other words, by disabling those optimizations we are making something that may (and it does) reduce the system performance. So the question is not if we will suffer lack of performance, but how much performance we will lose.
At the time I was writing this tip, a new piece of news emerged about Microsoft issuing an update to disable Intel’s patch for Spectre (https://www.cnbc.com/2018/01/29/microsoft-issues-update-to-disable-intels-buggy-spectre-patch.html) because sudden system reboots were reported.
Microsoft released a patch for the C++ compiler on Visual Studio 2017 version 15.5 that introduces the /Qspectre switch which is equivalent to the undocumented /d2guardspecload switch to disable speculative execution (https://blogs.msdn.microsoft.com/vcblog/2018/01/15/spectre-mitigations-in-msvc/). If you read the previous link you will find that Microsoft said this patch has a minimum impact on performance. Textually they said “Performance gains from speculative execution are lost where the mitigation is applied but the mitigation was needed in a relatively small number of instances across the large codebases that we recompiled. Codebases vary greatly so we advise all developers to evaluate the impact of /Qspectre in the context of their applications and workloads”.
But on the next screen capture of the previous link you will see that the resulting assembler code when compiling with /Qspectre has an extra instruction named LFENCE (short for Load Fence).
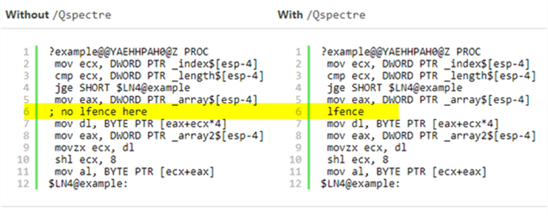
It is trivial that when a program adds an extra instruction then it should take longer to complete. That is without even considering that the extra instruction disables out-of-order execution which is a performance optimization technique.
There is no need to disable Out of Order Execution in all the applications. For example, an application that does not execute external code doesn’t need to disable Out of Order Execution. But a web browser that runs external code like JavaScript or SQL Server that runs Assemblies and Extended Stored Procedures needs to disable Out of Order Execution. But there is also good news, those applications that need to disable Out of Order Execution can do it on specific parts of the code.
What do we do?
First don’t panic and focus! If your system does not execute external code you don’t need to apply any patch, not even for Meltdown. On the other hand, if your system uses external sources you should patch it. Also if your system is a hypervisor you must patch it for Meltdown because you don’t know what code your VM hosts will run.
Next Steps
- This tip will help you to evaluate which of your SQL Servers needs patching: SQL Servers Assessment for the Meltdown and Spectre Vulnerabilities.
- Take a look at the SQL Server Security Tips Category.
- Stay tuned for more news about this issue.
About the author
 Daniel Farina was born in Buenos Aires, Argentina. Self-educated, since childhood he showed a passion for learning.
Daniel Farina was born in Buenos Aires, Argentina. Self-educated, since childhood he showed a passion for learning.This author pledges the content of this article is based on professional experience and not AI generated.
View all my tips
Article Last Updated: 2018-03-21






